ThreatGEN AutoTableTop™
Automated AI-Powered IR Tabletop Exercises.
ThreatGEN AutoTableTop™ is the most advanced tabletop exercise platform on the market. It is completely customizable, effortless to use, takes only minutes to setup, and has unlimited scenarios and possibilities right out of the box.
"Traditional" tabletops are limited by pre-scripted scenarios and injects, as well as the time and expertise it requires to plan and run them.
ThreatGEN AutoTableTop™ is powered by and automated with AI that is trained on threats and cybersecurity across multiple industries and domains. Setup is practically instantaneous and running exercises is effortless. Scenarios, injects, and entire exercises are automatically generated and facilitated (down to every last detail) by the AI according to your specifications. At the end of each exercise, a final report is generated, providing analysis, recommendations, and actionable tasks. Finally, AutoTableTop's ease of use allows your team to run as many scenarios as often as you like.
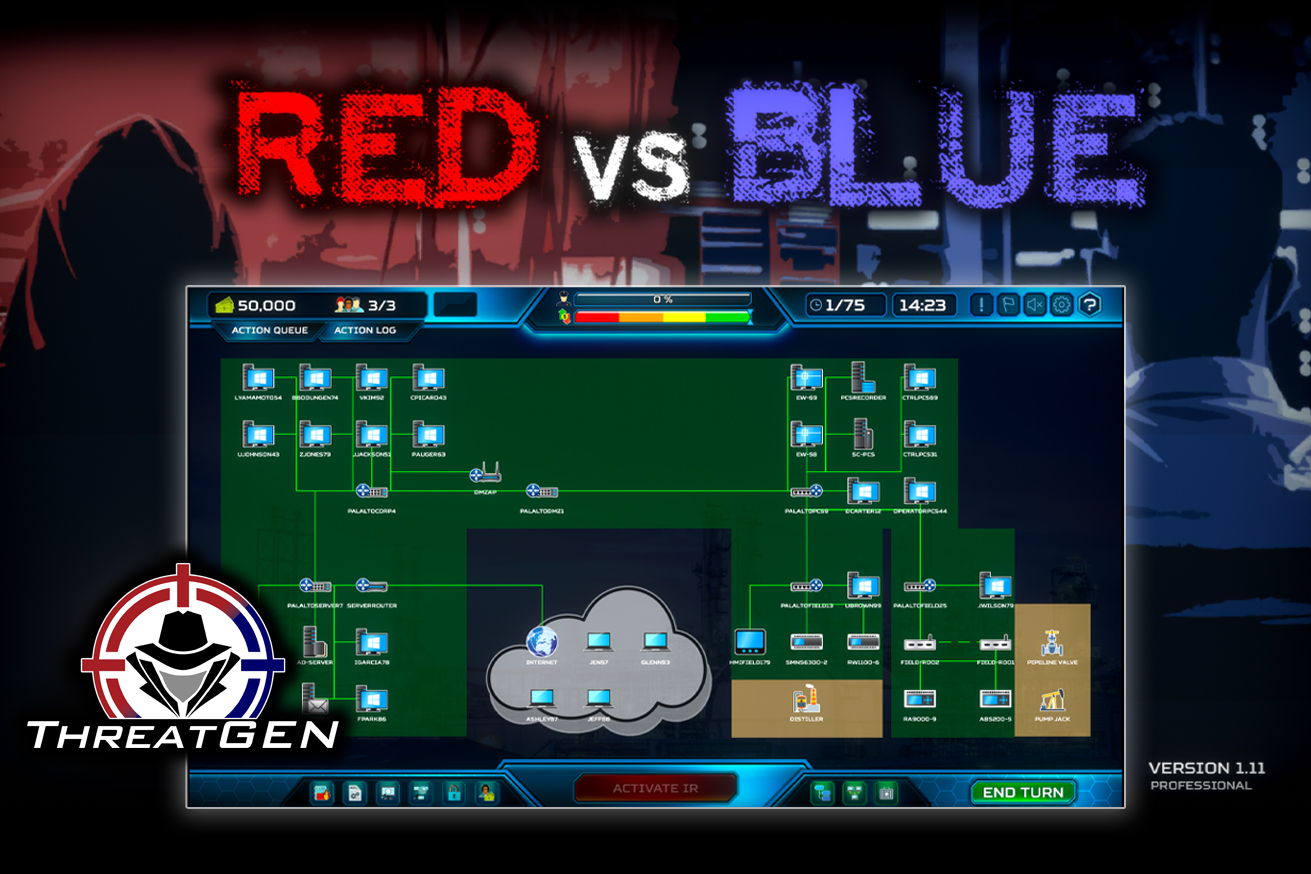
ThreatGEN® Red vs. Blue
Cybersecurity red team vs. blue team training has never been so fun.
ThreatGEN® Red vs. Blue is the next evolution in cybersecurity education, training, and IR tabletop exercises. It is a game-based cybersecurity simulation platform that combines the power of an actual computer gaming engine and adaptive adversary simulation A.I., to provide the most practical and effective way for ANYONE to learn cybersecurity, from beginners to experts, and even leadership. It doesn't require any prior technical knowledge or command line skills... not even to play as the red team! Used for cybersecurity education, awareness, training, and IR tabletop exercises, ThreatGEN® Red vs. Blue is immersive, interactive, and hands-on, and it's supported by an education portal with online courses, labs, scenarios, and an online community.
Our Clients