Summary
The “Call Center” scenario demonstrates a bustling call center environment, wherein customer service is paramount, and data security is critical. The network consists of various interconnected systems and assets, each playing a crucial role in the company’s daily operations.

Potential Vulnerabilities
- Outdated software on customer service workstations
- Weak password policies
- Unpatched VoIP system vulnerabilities
- Insufficient network segmentation
- Lack of multi-factor authentication for critical systems
- Potential for social engineering attacks due to high customer interaction
Briefings
Blue Team
Your mission is to secure your company’s network by improving your defences, reducing risk by implementing policies and managing and procuring staff and budget. Beginning with limited resources, you have your work cut out for you. You have more than enough tools to choose from, but they all come at a cost and take time to implement. You must choose your strategy carefully, however, because the Red Team is always lurking for a way in. Make a wrong move and you could find yourself shifting mission priority from defense to incident response.
You can win the game by doing any of the following:
- outlasting the Red Team when the turns expire
- eliminating all vulnerabilities within the assets on the network
- increasing the threat intelligence score to 100%
Red Team
Your mission is to perform reconnaissance, probe for weaknesses and find a way into the company’s network. Once inside, you’ll need to find a way to penetrate deeper into the network in search of the ultimate prize: critical process or financial assets. You could also plant malware and encrypt assets with ransomware to impact the profit of the company. Ultimately, you need to execute on your objective. It will require clever strategies, keen wit and every ounce of skill in your arsenal from social engineering to system exploitation. You might even need to research more advanced skills along the way to succeed…
You can win the game by doing any of the following:
- damaging the Blue Team’s critical process
- reducing the Blue Team’s profit/loss meter so that it stays in the red zone (below 25%) for 5 consecutive turns
Network Overview
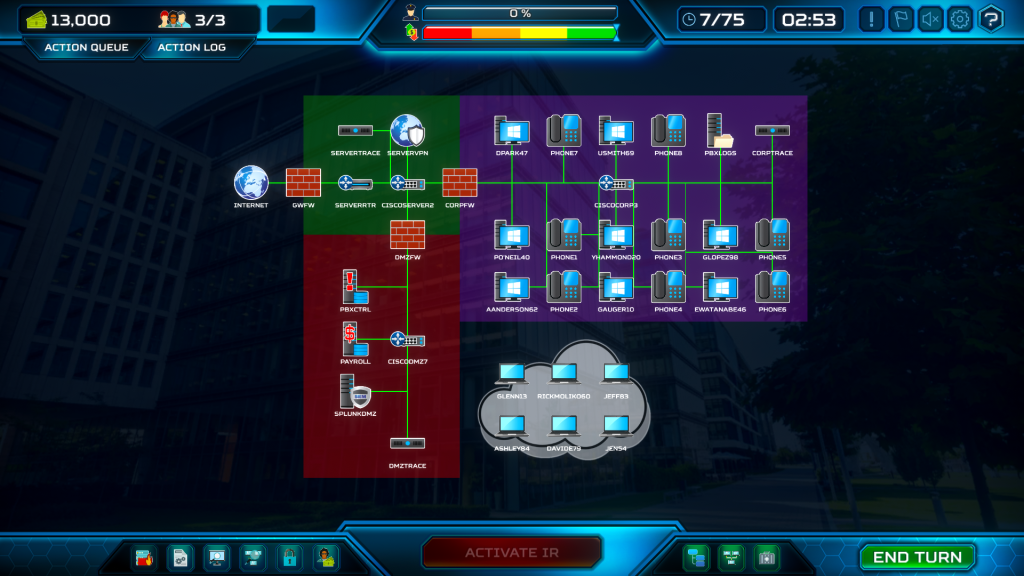
The call center network is divided into three main zones: Internet Gateway, Corporate Network, and Demilitarized Zone (DMZ). Each zone contains critical assets that support the call center’s operations and customer interactions.
- Internet Gateway
- Assets:
- GWFW: Gateway firewall that filters traffic between the internet and the internal network.
- ServerRtr: Gateway router: Used to route traffic between the LAN and the WAN.
- CISCOSERVER2: A switch connecting DMZ assets to the rest of the network..
- ServerVPN: Controls remote network access.
- ServerTrace: IDS, monitors network traffic.
- Purpose: Protects the internal network from external threats by controlling inbound and outbound traffic.
- Assets:
- Corporate Network (Purple Zone)
- Assets:
- Workstations (e.g., PO’NEIL40, DPARK47, etc.): Used by employees for daily operations.
- VoIP Phones (e.g., PHONE1, PHONE2): Essential for customer communication.
- PBXLogs: File server, stores call logs from the VoIP system.
- CISCOCORP3: A switch connecting Corporate Network assets to the rest of the network.
- CorpTrace: IDS, monitors network traffic.
- CorpFW: Firewall, restricts network traffic.
- Purpose: Supports core call center operations, including customer service, communication, and data management.
- Assets:
- Demilitarized Zone (DMZ) (Red Zone)
- Assets:
- PBXCtrl: Manages VoIP system configurations.
- Payroll Server: Handles employee payroll data.
- SplunkDMZ: Provides monitoring and logging capabilities for security events.
- CISCODMZ7: A switch connecting DMZ assets to the rest of the network.
- DMZFW: Firewall, restricts network traffic.
- DMZTrace: IDS, monitors network traffic.
- Purpose: Hosts services that require controlled access from both internal and external networks.
- Assets:
Released on Monday, February 10, 2025.
Copyright © 2025 by Derezzed Inc. D/B/A ThreatGEN, all rights reserved.
