What is ThreatGEN® Red vs. Blue?
ThreatGEN® Red vs. Blue is the next evolution in cybersecurity education. It is a game-based cybersecurity simulation platform that combines the power of an actual computer gaming engine and adaptive adversary simulation A.I., to provide the most practical and effective way for ANYONE to learn cybersecurity, from beginners to experts, and even leadership. It doesn't require any prior technical knowledge or command line skills... not even to play as the red team! Used for cybersecurity education, awareness, training, and IR tabletop exercises, ThreatGEN® Red vs. Blue is immersive, interactive, and hands-on, and it's supported by an education portal with online courses, labs, scenarios, and an online community.
Who uses ThreatGEN® Red vs. Blue?
- Businesses and Organizations
- Education and Training Providers
- Individual Cybersecurity Students and Professionals
- Event Coordinators

How ThreatGEN® Red vs. Blue benefits you.
Learn faster. Increase knowledge retention. Manage human-based risk.
A better educated and trained workforce is the most critical path to a stronger cybersecurity posture and lower human-based risk. ThreatGEN® Red vs. Blue maximizes learning retention and overall effectiveness through a more engaging hands-on approach. Our adaptive adversary simulation A.I. ensures students learn and understand both blue team and red team (attacker) methods, using practical application against an active and adaptive opponent, just as it will be in real life. Students, employees, leaders, and cybersecurity practitioners gain a much broader and more practical understanding of cybersecurity and will be better prepared to defend against real-world cyber threats.
How is ThreatGEN® Red vs. Blue being used by our clients?
- IR tabletop exercises
- Cybersecurity concepts and strategy education and training
- Cybersecurity awareness (human-based risk management)
- Cybersecurity training for leadership
- Team building
- CTF and tournament style competitions
How ThreatGEN® Red vs. Blue works.
The ThreatGEN® Red vs. Blue portal is web browser delivered and provides access to the cybersecurity simulation platform, on-demand courses, labs, and scenarios. Each course is a series of short video lessons covering specific cybersecurity concepts, which are reinforced through labs and scenarios in the form of a cybersecurity simulation and strategy game. Students increase their learning even further by playing matches against the computer opponent or online against other students or colleagues. Organizations can facilitate events with tournament, leaderboard, and IR tabletop exercise modes. Student and event, data, statistics, and historical trends are tracked through the analytics dashboard and reports.
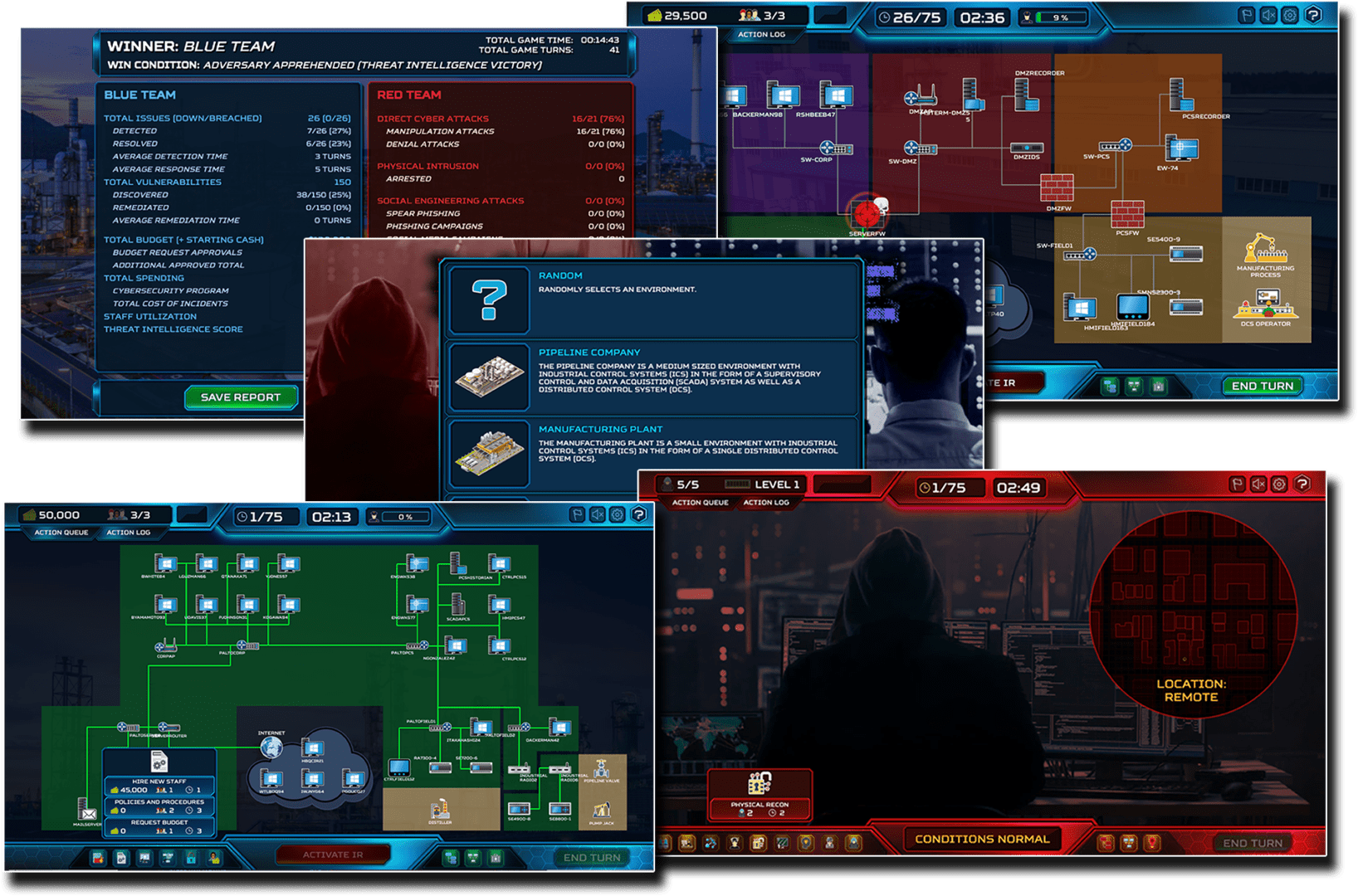
What makes ThreatGEN® Red vs. Blue so effective?






Adaptive Adversary Simulation A.I.
Cybersecurity isn't "set it and forget it." Adversaries are constantly trying to circumvent your defenses, requiring regular adjustments to your security controls and strategies. Our adaptive adversary simulation A.I. prepares you to defend against real-world threats using practical, “hands-on” application, against an opponent attempting to counter your every move.
Backed by Science
Using a hands-on approach combined with interactive game-based learning has been proven to be much more effective for learning retention and application compared to tradition education and training methods such as lectures and standard computer-based training (CBT).
Immersive & Interactive Game-Based Learning
Rather than quizzes, simple "games", and videos, ThreatGEN® Red vs. Blue is an immersive and interactive cybersecurity simulation platform. You interact with environments and scenarios, and learn by doing. It goes beyond "CTF" style challenges by introducing Adaptive Adversary Simulation A.I., where an opponent (computer or human) attempts to counter your every move.
IR Tabletop Exercise Scenarios
Traditional IR tabletop exercises are "paper based" (often supported by slides and spreadsheets). ThreatGEN® Red vs. Blue makes IR tabletop exercises more immersive, interactive, and entertaining using interactive game-based learning and visual environments. Additional realism is created using our Adaptive Adversary Simulation A.I. Running IR tabletop exercises has never been easier using our built-in "click and run" scenarios.
Practical Application for Cybersecurity Leadership & Strategic Skills
Not everyone learning cybersecurity requires the "hard" technical skills. Staff such as CISOs and managers require training in cybersecurity program management, and Governance, Risk, Management, and Compliance (GRC). In fact, these skills are often the foundation for other cybersecurity roles and certifications. ThreatGEN® Red vs. Blue not only helps you train in these areas, but does so through hands-on practical application using our game-based learning.
ICS/OT Integrated
Industrial control systems (ICS) and operational technology (OT) are becoming increasingly more targeted. ThreatGEN® Red vs. Blue co-founder and creator, Clint Bodungen, has nearly 2 decades in the ICS/OT cybersecurity industry, and is the lead author of Hacking Exposed: Industrial Control Systems. His experience and direction have gone into ThreatGEN® Red vs. Blue to create ICS/OT environments, content, and scenarios.
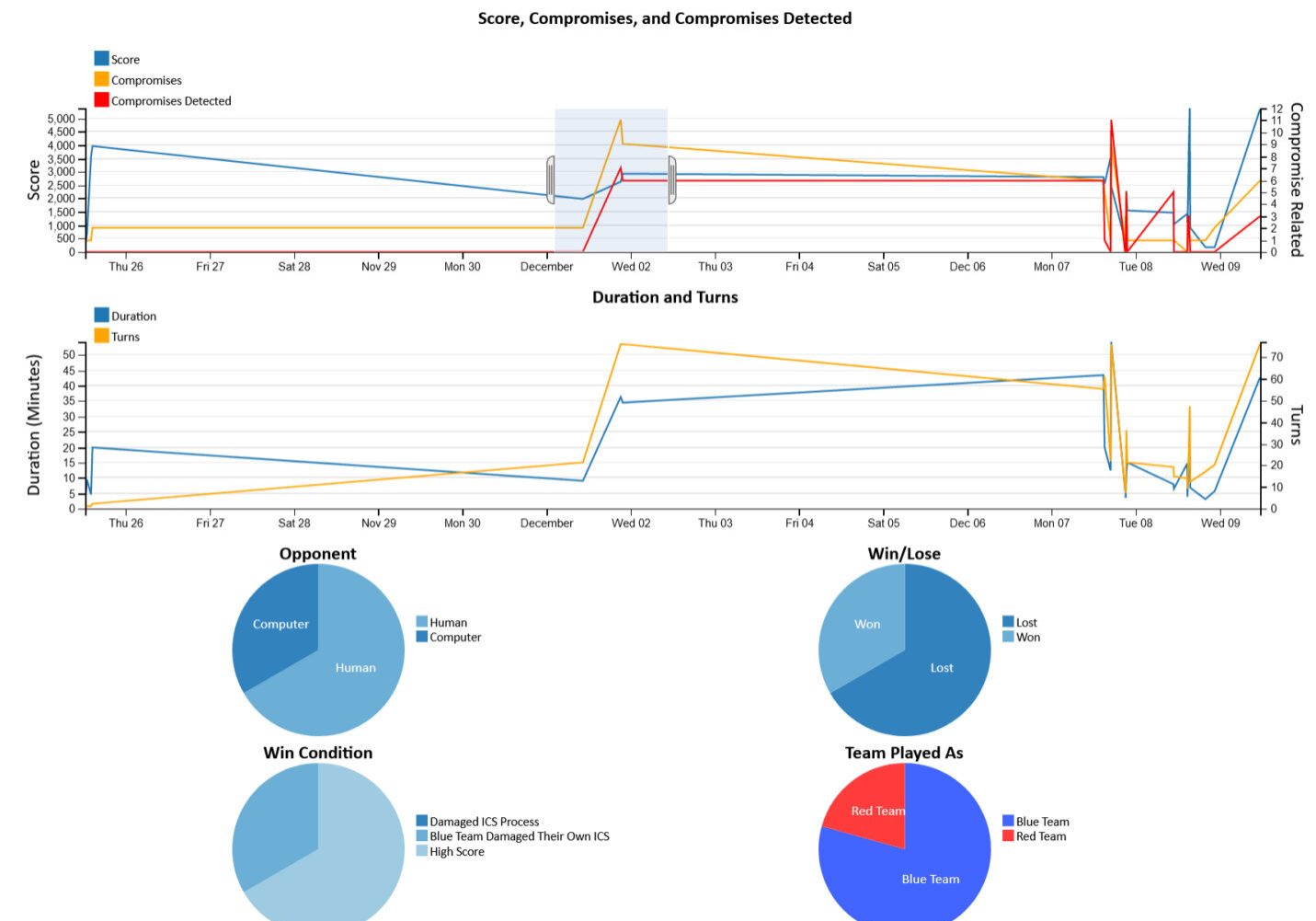
Performance Metrics and Analytics
ThreatGEN® Red vs. Blue includes invaluable metrics, analytics dashboards, and reporting for measuring and evaluating student progress and performance. It helps organizations manage their human-based risk and improve their cybersecurity program by tracking results from cybersecurity awareness training and technical staff training.
