Summary
A leading biomedical research institution (“The Institute“) dedicated to advancing human health through genomic research and animal models has detected unusual network activity. The Institute is renowned for its work in genetics, cancer research, and immunology, contributing significantly to global medical advancements.
A sophisticated state-sponsored threat actor is attempting to infiltrate The Institute‘s network with the aim of exfiltrating sensitive research data related to “Project Chimera,” a highly confidential study involving cutting-edge gene-editing techniques and animal modeling (sound familiar for movie buffs interested in impossibly hard missions). This project has the potential to revolutionize the treatment of genetic diseases, making it a high-value target.

Potential Vulnerabilities
With such a complicated environment, there are innumerable attack surfaces to contemplate but here are a few important vulnerabilities:
- Insufficient segmentation between
- Weak or outdated credentials on key servers
- Lack of endpoint detection and response (EDR) solutions on critical workstations
- Unpatched vulnerabilities
- Limited monitoring or logging
Briefings
Blue Team Briefing
Your mission is to safeguard the integrity of “Project Chimera“, a groundbreaking research initiative housed within The Institute‘s laboratory network. This project, which leverages advanced genomic sequencing and gene-editing technologies, is critical to advancing treatments for genetic disorders. The stakes are high: any breach of the laboratory network could result in the theft of proprietary data, disruption of sensitive research operations, and reputational damage to The Institute.
Your primary focus will be on ensuring the security of key assets. Vigilance is required across all zones to detect and neutralize threats before they compromise Project Chimera. As always with ThreatGEN® Red vs. Blue, you can win the game by doing any of the following:
- outlasting the Red Team when the turns expire
- eliminating all vulnerabilities within the assets on the network
- increasing the threat intelligence score to 100%
With this extensive network map and scenario, here are additional goals:
- Prevent Data Exfiltration: Ensure that no Project Chimera files are accessed on the LAB-FILES server or other laboratory nodes.
- Maintain System Availability: Protect critical systems like DNA sequencers and laboratory workstations to avoid disruptions in ongoing research operations.
- Neutralize Threats: Identify intrusions early using tools like SIEMDMZ and CORPNIDS and take immediate action to contain and remediate any breaches.
Success depends on proactive threat detection, robust defense strategies across all network zones, and swift incident response to secure The Institute‘s invaluable research data.
Red Team Briefing
Your mission is to infiltrate The Institute‘s network and compromise “Project Chimera“, a highly sensitive research initiative focused on cutting-edge genomic sequencing and gene-editing technologies. This project represents a breakthrough in the treatment of genetic disorders, making it a prime target for exfiltration and disruption.
The Institute has implemented layered defenses across its corporate, DMZ, and laboratory networks, but vulnerabilities remain. Your objective is to exploit these weaknesses, gain access to critical systems, and achieve your operational goals before the defenders can neutralize your efforts. As always with ThreatGEN® Red vs. Blue, you can win the game by doing any of the following:
- Damaging the Blue Team’s critical process
- Reducing the Blue Team’s profit/loss meter so that it stays in the red zone (below 25%) for 5 consecutive turns
Since you have been engaged by a state-sponsored threat actor for this mission, here are some additional goals:
- Exfiltrate Project Chimera Data: Locate and extract sensitive files stored on the servers or other laboratory nodes.
- Disrupt Laboratory Operations: Compromise DNA sequencers or laboratory workstations to hinder ongoing research activities.
- Establish Persistence: Gain control of key systems to maintain long-term access to the network.
Success will require stealth, precision, and persistence. Leverage reconnaissance to identify vulnerabilities, escalate privileges through compromised nodes, and execute your objectives while minimizing detection by the Blue Team.
Review of Network
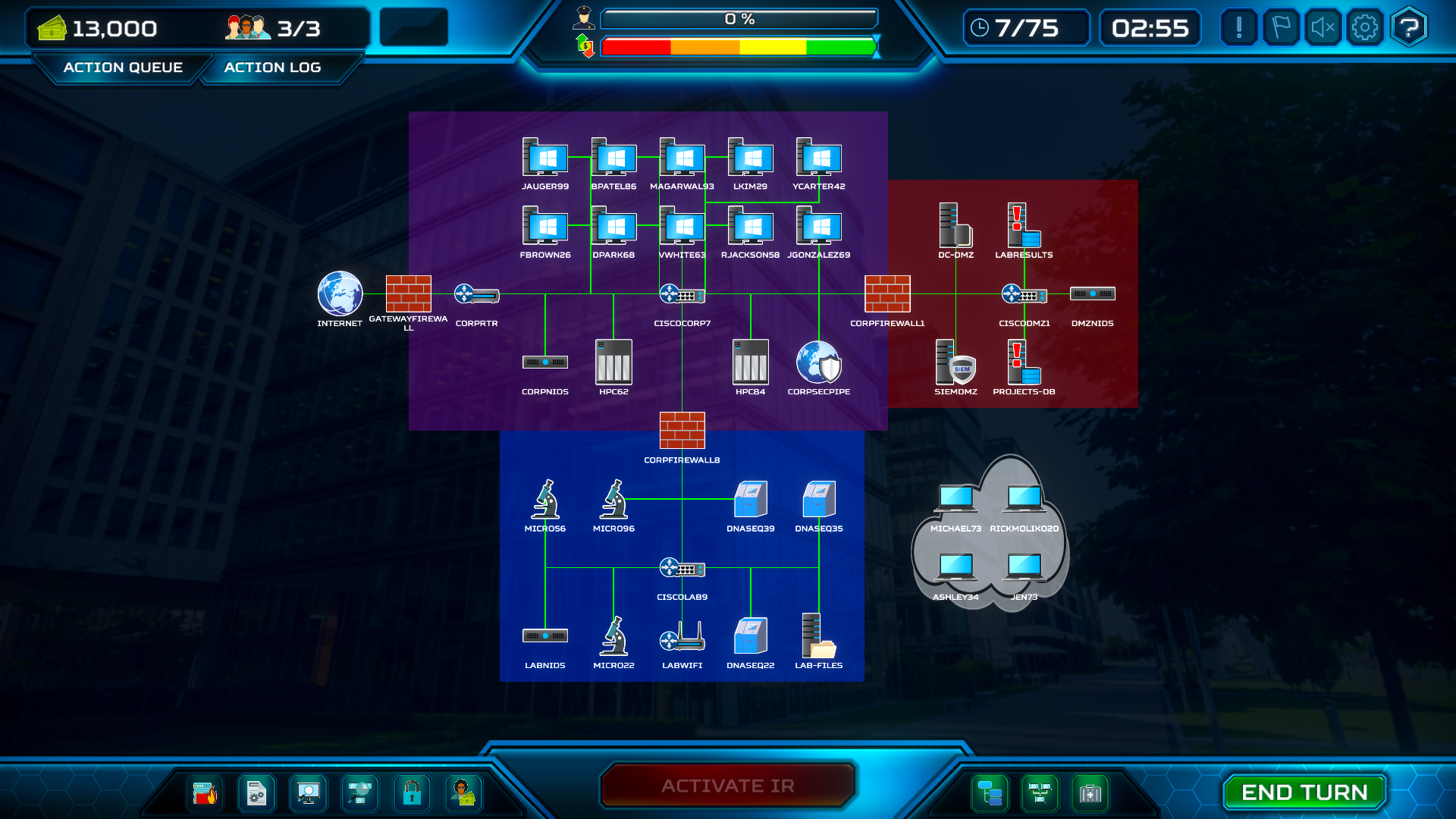
The network is segmented into three zones:
- Corporate Network (Purple Zone): The primary entry point, hosting staff workstations, network detection systems (CORPNIDS), high-performance computing resources (HPC40), and VPN access (CORPVPN).
- DMZ (Red Zone): A critical intermediary zone where the Active Directory server (AD-DMZ), SIEM system (SIEMDMZ), and Projects Database (PROJECTS-DB) are located. This is where Project Chimera data resides.
- Laboratory Network (Blue Zone): The most secure zone containing research equipment (DNA sequencers, microscopes), the LAB-FILES server, and wireless access points.
Scenario released on Thursday, March 6, 2025, original map released March 3, 2025.
Copyright © 2025 by Derezzed Inc. D/B/A ThreatGEN, all rights reserved.
