A major American car manufacturing facility (“The Plant“) that produces vehicles for the domestic and international markets has detected unusual network activity within its industrial control systems. The Plant is renowned for its advanced robotics, just-in-time production systems, and innovative electric vehicle development, contributing significantly to American manufacturing leadership.
Summary
A sophisticated foreign car manufacturing company is attempting to infiltrate The Plant’s network with the aim of exfiltrating sensitive data related to “Project Electra“, a highly confidential initiative involving cutting-edge electric vehicle battery technology and proprietary manufacturing processes. This project has the potential to revolutionize the automotive industry with breakthrough efficiency in electric vehicle production, making it a high-value target for industrial espionage.
The car manufacturing facility utilizes advanced industrial control systems (ICS) in the form of a Supervisory Control and Data Acquisition (SCADA) system and a Distributed Control System (DCS) to manage its complex production environment. The network infrastructure spans multiple security zones with varying levels of access control.

Potential Vulnerabilities
With such a complex manufacturing environment, there are numerous attack vectors to consider:
- Insufficient segmentation between IT networks and operational technology (OT) systems
- Weak or outdated credentials on key SCADA and DCS controllers
- Lack of endpoint detection and response (EDR) solutions on engineering workstations
- Unpatched vulnerabilities in industrial control systems
- Inadequate security monitoring of manufacturing floor activities
- Aging PLCs (Programmable Logic Controllers) with outdated firmware
- Poor security controls between network zones visible in the system architecture
Briefings
Blue Team Briefing
Your mission is to safeguard the integrity of “Project Electra“, a groundbreaking initiative housed within The Plant’s manufacturing network. This project represents American leadership in electric vehicle technology and innovative production methods, critical to maintaining competitive advantage in the global automotive market.
The stakes are high: any breach could result in theft of proprietary designs, disruption of production operations, and significant financial and reputational damage to American manufacturing capabilities.
Your primary focus will be securing key assets across all network zones shown in the network map. You can win this exercise by:
- Outlasting the Red Team when the turns expire
- Eliminating all vulnerabilities within the assets on the network
- Increasing the threat intelligence score to 100%
Additional Goals
In addition to the generalized goals above, this scenario requires much more:
- Protect Intellectual Property: Ensure that no Project Electra files are accessed on the file servers or engineering workstations visible in the purple and blue zones.
- Maintain Production Continuity: Protect critical systems like assembly controllers and robotics workstations to prevent disruptions to vehicle production.
- Preserve Control System Integrity: Safeguard SCADA and DCS systems from tampering that could compromise safety or quality in the manufacturing process.
- Neutralize Threats: Identify intrusions early using monitoring tools and take immediate action to contain and remediate any breaches before they reach critical OT systems.
Success depends on proactive threat detection, robust defense strategies across all network zones, and swift incident response to secure The Plant’s valuable manufacturing data and operational continuity.
Red Team Briefing
Your mission is to infiltrate The Plant’s network and compromise “Project Electra“, a highly sensitive initiative focused on next-generation electric vehicle technology. This project represents a significant advantage in the global automotive industry, making it a prime target for your foreign automotive competitor client.
The Plant has implemented layered defenses across its corporate, DMZ, and operational technology networks as shown in the network diagram, but vulnerabilities remain. Your objective is to exploit these weaknesses, gain access to critical systems, and achieve your operational goals before the defenders can neutralize your efforts.
You can win this exercise by:
- Damaging the Blue Team’s critical manufacturing processes
- Reducing the Blue Team’s profit/loss meter so that it stays in the red zone (below 25%) for 5 consecutive turns
- Establishing persistence within the network for continued intelligence gathering
Additional Objectives
This scenario’s objectives for the Red Team underscores how corporate espionage depends more and more upon cyber compromises. Additional objectives include:
- Exfiltrate Project Electra Data: Locate and extract sensitive files stored on the engineering servers or design workstations visible in the network map.
- Disrupt Manufacturing Operations: Compromise assembly line controllers or robotic systems to hinder ongoing production activities and create costly downtime.
- Manipulate Quality Control: Subtly alter parameters in the SCADA systems to create defects that will only be discovered after vehicles reach the market, damaging brand reputation.
- Establish Persistence: Gain control of key systems to maintain long-term access to the network for continued intelligence gathering on future vehicle designs.
Success will require stealth, precision, and persistence. Leverage reconnaissance to identify vulnerabilities, escalate privileges through compromised nodes, and execute your objectives while minimizing detection by the Blue Team.
Review of Network
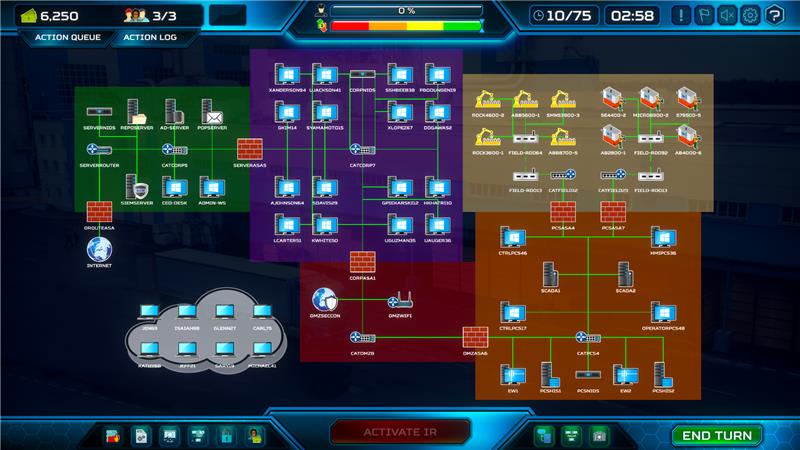
The car manufacturing facility’s network is structured into several distinct segments, each with specialized functions and security considerations.
Please note that most of the zones do not show up as different colors until the Blue Team segments the network. Prior to that, everything is in the same zone except the shop floor.
The following overview reflects the revised color-coded zones and their operational roles, as depicted in the attached network map:
- Green Zone – Server Segment (External Communications): This segment houses the primary servers that require communication with the outside world, such as internet-facing services, supply chain integrations, and vendor portals. These systems are essential for business operations that depend on real-time data exchange with external partners and remote support teams.
- Purple Zone – Administrative IT Workstations: Contains all administrative and IT-related user workstations. These are used by internal staff for day-to-day business operations, management tasks, and access to internal applications. This zone is a common target for phishing and credential theft, as it often serves as a bridge between the corporate network and more sensitive areas.
- Red Zone – DMZ for Cloud and Wi-Fi Communications: This demilitarized zone acts as a buffer between the internal network and external services, including cloud platforms and wireless networks. It is designed to securely handle traffic to and from the cloud, as well as manage Wi-Fi access points. The DMZ is a frequent target for attackers seeking initial entry, making robust segmentation and monitoring essential.
- Orange Zone – Operations Technology Network (Most Critical): The heart of the facility, this zone contains the most security-sensitive assets: SCADA servers, Human-Machine Interfaces (HMIs), Programmable Logic Controllers (PLCs), and other physical control systems that directly manage manufacturing processes. Compromise here could result in operational disruption, safety incidents, or sabotage of production lines. This is the highest-priority area for cybersecurity defenses.
- Tan Zone – Shop Floor: Encompasses manufacturing execution systems, and field servers. This zone is responsible for translating business logic into physical production activities, making it a key target for attacks aiming to disrupt or manipulate manufacturing output.
This segmentation highlights the layered defense model required for modern automotive manufacturing, where each zone presents unique attack surfaces and requires tailored security controls. The Operations Technology Network (Red/Orange) remains the most critical, demanding the highest level of protection due to its direct impact on physical processes and overall plant safety.
Scenario released on Thursday, April 24, 2025, and original map released to production on Wednesday, April 15, 2025, with revisions on April 24, 2025.
Copyright © 2025 by Derezzed Inc. D/B/A ThreatGEN, all rights reserved.
