Summary
The agricultural plant factory & store (“Factory & Store“) is a sprawling, digitally integrated manufacturing environment (one of the largest in ThreatGEN® Red vs. Blue version 1.x). It leverages advanced Industrial Control Systems (ICS), including Supervisory Control and Data Acquisition (SCADA) and Distributed Control Systems (DCS), to automate production and manage logistics. The network map reveals a complex web of interconnected OT (Operational Technology) and IT assets, spanning from field devices and PLCs to business systems and remote access point.

Recent Threat Landscape (May 2025)
The manufacturing, and as a by-product agricultural and food manufacturing, sectors has become the prime target for ransomware attacks. In Q4 2024, 70% of all ransomware incidents in industrial sectors struck manufacturing, causing widespread operational disruptions, data theft, and significant financial losses (Manufacturing sector hit hardest by ransomware in 2024 Q4). Attackers are increasingly sophisticated, blending phishing, supply chain compromise, and exploitation of exposed ICS devices to gain access and deploy ransomware payloads (Cyber security 101 for the manufacturing industry).
Real-World Precedent
In 2023, MKS Instruments-a major semiconductor equipment manufacturer-was crippled by a ransomware attack. The breach forced the company to take critical systems offline, revert to manual processes, and resulted in a $200 million revenue shortfall for the quarter. The attack also rippled through its supply chain, impacting customers like Applied Materials, which reported a $250 million dip in sales due to the disruption (see “Cybersecurity 101 for the manufacturing industry” article above for information on this and other similar attacks). This incident exemplifies the cascading consequences of cyberattacks in highly connected manufacturing environments.

Briefings
Blue Team Briefing
Your mission is to defend the Plant Factory & Store’s complex ICS environment from an escalating ransomware campaign. With limited resources, you must:
- Harden network segments, especially those connecting OT and IT.
- Patch vulnerabilities in SCADA, DCS, and PLC devices.
- Train staff to recognize and resist phishing and social engineering.
- Implement robust backup and recovery procedures.
- Monitor for lateral movement and signs of compromise.
Convincing management for additional budget is possible but challenging. Every decision comes with trade-offs in cost, time, and risk. The Red Team is persistent – one misstep could force a shift from proactive defense to full-scale incident response! Victory for the Blue Team will be a challenge with the sheer scale of this environment:
- Eliminate all critical vulnerabilities.
- Achieve 100% threat intelligence coverage.
- Outlast the Red Team through the scenario’s turn limit.
Red Team Briefing
Your objective is to breach the Plant Factory & Store’s defenses and unleash ransomware within its ICS environment.
- Conduct reconnaissance to identify exposed assets and weak points-especially in remote access, supply chain connections, or unpatched PLCs.
- Use phishing, supply chain compromise, or exploit known ICS vulnerabilities to gain initial access.
- Move laterally, escalate privileges, and deploy ransomware to disrupt production and exfiltrate sensitive data.
Remain stealthy to avoid early detection. Consider targeting backup systems to maximize impact and force the Blue Team into costly recovery efforts.
With such a large environment with so much complexity, the Red Team’s victory conditions will give it an edge over the Blue Team. Victory will require:
- Cause operational disruption by encrypting or damaging ICS assets.
- Drive the profit/loss meter into the red for five consecutive turns by denying key assets and exfiltrating data.
Review of the Network
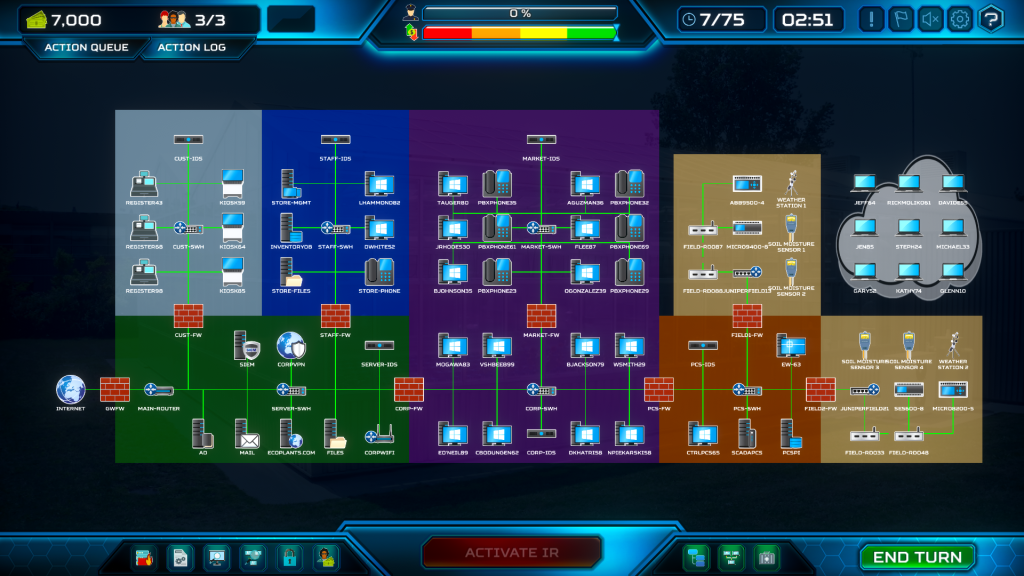
The network environment displayed shows a comprehensive industrial control system (ICS) setup for the Plant Factory & Store, organized into distinct color-coded zones that represent different functional areas of the operation.
- Light Blue Zone – Customer facing environment: Point-of-sale systems including multiple registers (REGISTER3, REGISTER8, REGISTER9), customer kiosks (KIOSK98, KIOSK94, KIOSK95) for self-service. This zone is protected by a dedicated customer firewall (CUST-FW) and IDS (Intrusion Detection System) while connected to the main router which provides internet connectivity.
- Blue Zone – Staff and store operations: Zone housing inventory management and administrative systems, containing STORE-MGMT, INVENTORY08, STAFF-SWH (staff switch) components, store files server and staff phones visible in this segment while segregated by its own firewall (STAFF-FW) for security separation.
- Purple Zone – Corporate and marketing systems: Multiple workstations and communication devices featuring marketing-specific servers and corporate workstations, multiple desk phones integrated into the network infrastructure. Protected by corporate firewalls (CORP-FW) and has its own IDS (MARKET-IDS).
- Brown Zone – Manufacturing Controls: Process control systems (PCS) zone containing SCADA (Supervisory Control and Data Acquisition) components, operational technology elements that directly interface with field devices, and CTRLPCSS, SCADAPCS and other control systems visible in this segment. Critical junction between IT and OT (Operational Technology) systems.
- Tan Zone – Manufacturing: Field operations zone containing environmental monitoring systems, weather stations and soil moisture sensors for agricultural monitoring, FIELD-ROD systems and specialized sensing equipment, and JUNIPER-FIELD3 components for field operations management.
The security architecture implemented in this network map includes:
- Segmented zones separated by firewalls (shown as brick wall icons)
- Dedicated intrusion detection systems for each operational area
- Hierarchical structure with controlled data flows between zones
VPN infrastructure for secure remote access (CORPVPN)
This environment represents a modern industrial control network that combines traditional IT systems with operational technology, creating a complex attack surface that requires sophisticated security controls and monitoring.
Scenario released Friday, May 2, 2025, and original map released Tuesday, April 1, 2025 (no April Fools here).
Copyright © 2025 by Derezzed Inc. D/B/A ThreatGEN, all rights reserved.
