Summary
Inspired by the SolarWinds incident, our team has decided to build an amazing IT Management Software Development Company environment. Will you penetrate the software development company to compromise their software and execute a global-scale software supply-chain compromise?
Can you turn fate around and defend your network from various threats? Only time will tell…
NOTE: This scenario's network map is not meant to represent any SolarWinds' locations. Any similarities to actual corporate network environments are purely coincidental.
For more information on the SolarWinds cybersecurity incident, see our AutoTableTop™ SolarWinds scenario.
Potential Vulnerabilities Related to SolarWinds Incident
The SolarWinds cybersecurity incident involved attackers compromising the supply chain by injecting malicious code into legitimate software updates. This allowed them to infiltrate networks undetected. Similar vulnerabilities in this network could include:
Compromised Software Supply Chain
- Vulnerable Points
- Systems like
CORPORATE-SIEMorCORPORATE-ADcould be compromised if they rely on third-party software or updates. - Development servers (
DEV01,DEV02) might be used to test or deploy software updates, making them targets for supply chain attacks.
- Systems like
- Mitigation
- Implement strict code-signing policies.
- Regularly audit third-party software dependencies.
Insufficient Network Segmentation
- Vulnerable Points
- If firewalls between segments (e.g.,
MGMT-FW,DEVOPS-FW) are misconfigured or have weak rules, attackers could move laterally across the network. - Shared resources like
STAFF-FILESmight provide a pivot point for attackers.
- If firewalls between segments (e.g.,
- Mitigation
- Enforce strict access controls between segments.
- Use micro-segmentation to limit lateral movement.
Privileged Account Abuse
- Vulnerable Points
- Active Directory (
CORPORATE-AD) is a critical target for attackers seeking privileged access. - Remote users in the cloud environment might have elevated permissions that could be exploited.
- Active Directory (
- Mitigation
- Implement multi-factor authentication (MFA) for all privileged accounts.
- Regularly review and minimize privileged access.
Remote Access Exploitation
- Vulnerable Points
- The internet gateway is a potential entry point for attackers targeting remote workers or outdated VPN configurations.
- Devices in the cloud environment might lack endpoint protection.
- Mitigation
- Use secure VPNs with up-to-date encryption protocols.
- Deploy endpoint detection and response (EDR) solutions.
Weak Monitoring and Detection
- Vulnerable Points
- If IDS systems (
CORP-IDS,LAB-IDS, etc.) are not properly tuned, they may fail to detect anomalous activity. - SIEM systems might miss subtle indicators of compromise if logs are incomplete or poorly analyzed.
- If IDS systems (
- Mitigation
- Regularly update IDS signatures and SIEM correlation rules.
- Conduct periodic threat-hunting exercises.
By addressing these vulnerabilities, the organization can reduce its risk of falling victim to attacks similar to the SolarWinds incident.
Briefings

Blue Team
The date is December 13, 2020. A large IT Management Software Development Company reports that a cybersecurity issue is affecting some of its software, promptly publishing an update to remove the backdoor. The alleged attack vector is password guessing, password spraying, and inappropriately secured administrative credentials accessible via external remote access services, which the attackers could use to install the malware, ultimately inserting the backdoor into its IT management platform and compromising thousands of companies via a software supply-chain compromise. Russian intelligence is suspected to be behind the attack, likely intending to enhance its espionage capabilities and to establish footholds within other governmental networks.
Your mission is to secure this large IT Management Software Company by improving your defenses, reducing risk by implementing policies, as well as managing staff and budget. Much like the Russian intelligence, the threat actors are always looking for a way in. Will you identify weak and default credentials in your environment and install a VPN to prevent an incident like this or use any of the other tools at your disposal?
You can win the game by doing any of the following:
- eliminating all vulnerabilities within the assets on the network
- increasing the threat intelligence score to 100%
- outlasting the Red Team when the turns expire
Red Team
A large IT Management Software Development Company reports that on December 13, 2020, a cybersecurity issue is affecting some of its software, promptly publishing an update to remove the backdoor. The alleged attack vector has been password guessing, password spraying, and inappropriately securing administrative credentials accessible via external remote access services, which the attackers can use to install malware, ultimately inserting the backdoor into its IT management platform and compromising thousands of companies via a software supply-chain compromise. Russian intelligence is suspected to be behind the attack, likely intending to enhance its espionage capabilities and to establish footholds within other governmental networks.
As the Red Team, your mission is to execute the entirety of an attack kill chain in other to accomplish your objectives. Will you be able to gain initial access via password-based attacks, just like the Russian intelligence, and install malware in the environment to compromise the company’s software or will you choose to find some other critical process to destroy?
You can win the game by doing any of the following:
- damaging the Blue Team’s critical process
- reducing the Blue Team’s profit & loss meter so that it stays in the red zone (below 25%) for 5 consecutive turns
Network Overview
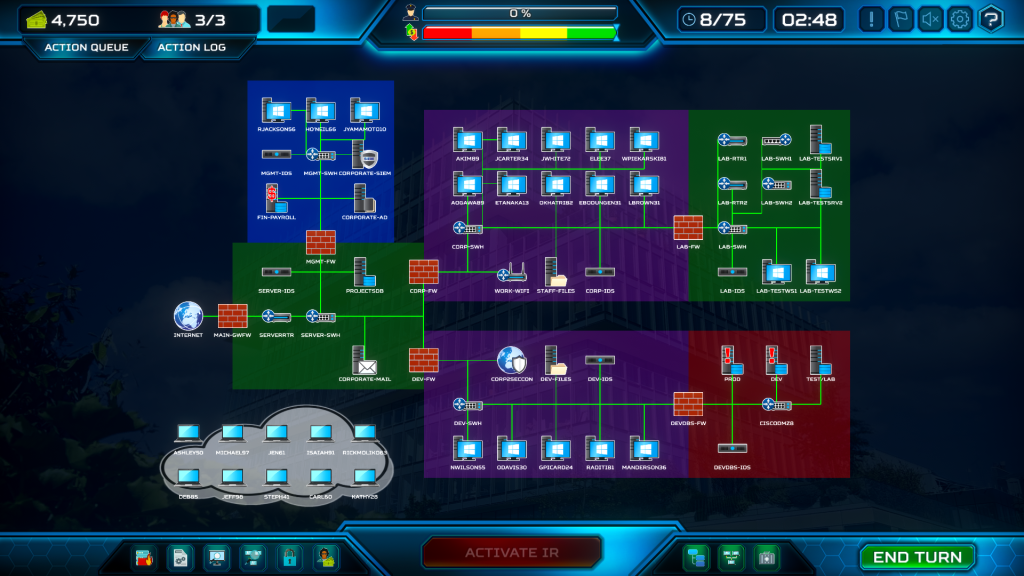
This network map represents a complex IT infrastructure for a large software company. The map illustrates multiple network segments (corporate, development, laboratory, and cloud environments) with firewalls and intrusion detection systems (IDS) separating them. Here’s a discussion on the different network segments:
Corporate Segment – Blue and Purple Zones
- Assets:
- User workstations (e.g.,
R.JACKSONS6,AKIMB9) - Key servers like
CORPORATE-AD(Active Directory) andCORPORATE-SIEM - Financial systems (
FIN-PAYROLL) and shared resources (STAFF-FILES)
- User workstations (e.g.,
- Segmented by:
- Firewalls (
MGMT-FW,CORP-FW) and IDS
- Firewalls (
Development Segment – Red Zone
- Assets:
- Hosts development servers (
DEV01,DEV02) - Test environments (
TEST-LAB)
- Hosts development servers (
- Segmented by:
- Firewalls (
DEVOPS-FW) and IDS
- Firewalls (
Laboratory Segment – Green Zone
- Assets:
- Lab routers
- Switches
- Test servers (
LAB-TESTSRV1,LAB-TESTSRV2)
- Segmented by:
- Firewalls (
LAB-FW)
- Firewalls (
Cloud Environment
- Assets:
- Remote users with individual devices (e.g.,
ASHLEY50,MICHAEL97)
- Remote users with individual devices (e.g.,
- Segmented by:
- Connected to the corporate network via the internet gateway
Scenario released on Thursday, February 21, 2025, original map released September 21, 2024.
Copyright © 2025 by Derezzed Inc. D/B/A ThreatGEN, all rights reserved.
