Posts Tagged ‘ThreatGEN® Red vs. Blue’
ThreatGEN® Red vs. Blue Version 1.11.25 Released: A Leap Forward into AI-Powered Development and Content Creation
Get ready for faster, more impactful updates from ThreatGEN® Red vs. Blue! With version 1.11.25, we’re making a profound shift to an AI-assisted development methodology, utilizing the same cutting-edge AI and LLM technologies powering AutoTableTop™ 2.0. This means more efficient feature development, richer content creation, and an improved user experience on the horizon. Learn how this transformative shift benefits you, our community!
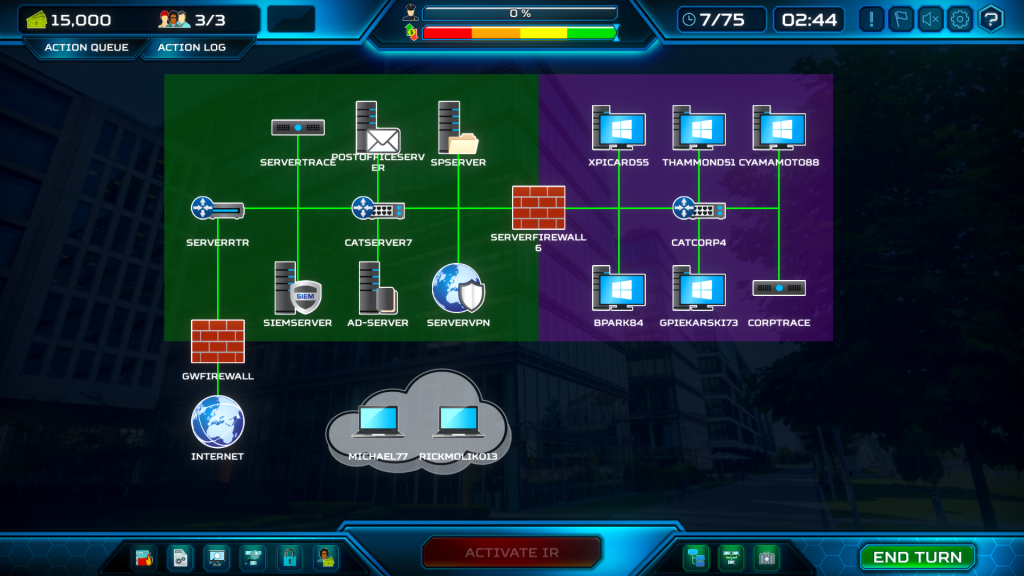
Read MoreAgricultural Factory & Plant Red vs. Blue Scenario
The Plant Factory & Store is a sprawling, digitally integrated manufacturing environment (one of the largest in ThreatGEN® Red vs. Blue version 1.x). It leverages advanced Industrial Control Systems (ICS), including Supervisory Control and Data Acquisition (SCADA) and Distributed Control Systems (DCS), to automate production and manage logistics. The network map reveals a complex web of interconnected OT (Operational Technology) and IT assets, spanning from field devices and PLCs to business systems and remote access point.
Read MoreCar Manufacturing Facility Red vs. Blue Scenario
A major American automotive manufacturing facility (“The Plant”) that produces vehicles for the domestic and international markets has detected unusual network activity within its industrial control systems. The Plant is renowned for its advanced robotics, just-in-time production systems, and innovative electric vehicle development, contributing significantly to American manufacturing leadership.
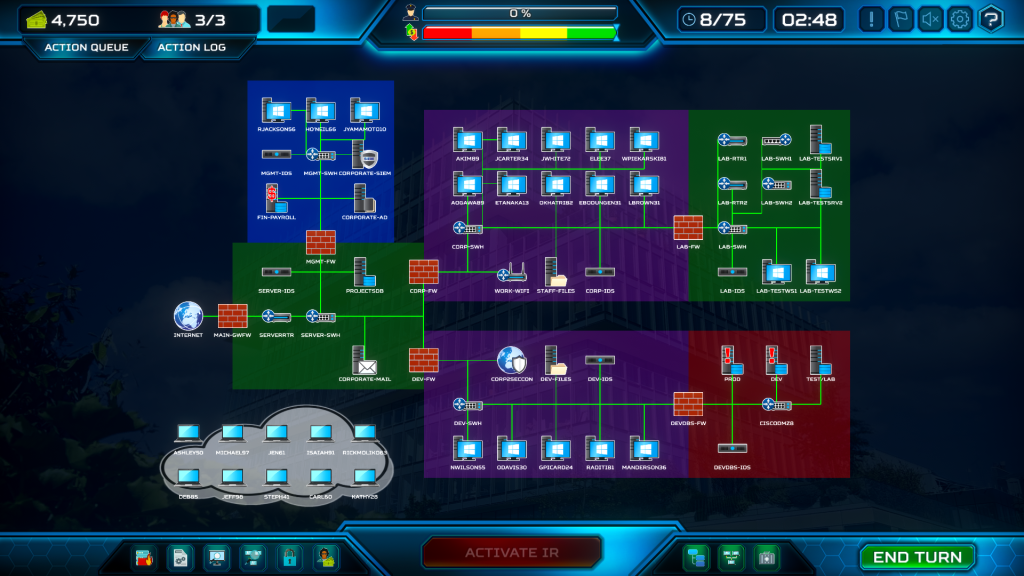
Read MoreActive Directory and other nodes in ThreatGEN® Red vs. Blue
ThreatGEN® Red vs. Blue capabilities associated with specific network node types, such as Active Directory nodes. Limitations and specific examples are included in this often asked FAQ.
Read MoreRed vs. Blue Environments Available
This FAQ details the different ThreatGEN™ Red vs. Blue network environments and scenarios that are available.
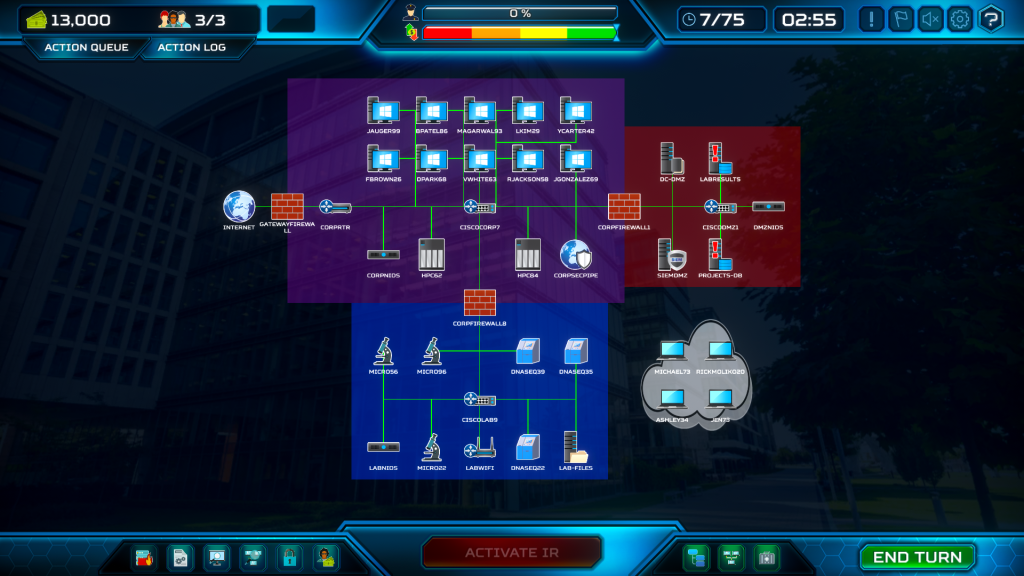
Read MoreResearch Laboratory Red vs. Blue Scenario
A leading biomedical research institution (“The Institute”) dedicated to advancing human health through genomic research and animal models has detected unusual network activity. The Institute is renowned for its work in genetics, cancer research, and immunology, contributing significantly to global medical advancements.
Read MoreIT Management Software Development Company, Red vs. Blue Scenario
Inspired by the SolarWinds incident, our team has decided to build an amazing IT Management Software Development Company environment.
Read MoreCall Center Red vs. Blue Scenario
The “Call Center” ThreatGEN® Red vs. Blue scenario demonstrates a bustling call center environment, wherein customer service is paramount, and data security is critical.
Read MoreBlue Team – Recovering from Ransomware
Within the Blue Team game play, how do I remove ransomware if it is already present and active? More importantly, how do I prevent it from being installed in the first place?
Read MoreRed Team – attack detection evasion
From the Red Team’s perspective, does the “Attack Detection Evasion” actually work? Walk through how this action to evade the Blue Team’s IDS sensors and EDR works for the Red Team.
Read More