Bloom’s taxonomy is widely recognized as a utility for developing learning objectives for students and allowing these objectives to be properly mapped to learning levels that are appropriate. It allows educators to enable students to build upon basic learning elements ultimately developing higher-level thinking.
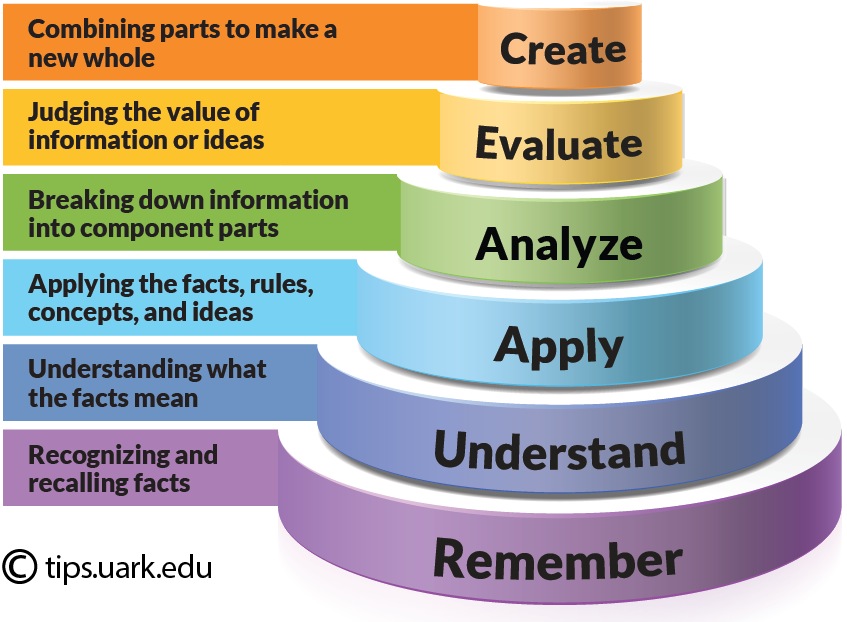
Cybersecurity as a discipline has a multitude of learning opportunities, but do they result in actual acquisition of knowledge. Higher education organizations may map lecture with labs, but without Bloom’s taxonomy to assure alignment, students may be missing the transformation that comes from assimilating lessons learned.
ThreatGEN® Red vs. Blue
The ThreatGEN® Red vs. Blue Cybersecurity Simulation Game-Based Learning Platform provides an opportunity for students to immerse themselves in the role of an attacker or defender and appreciate the impact and complexities that result from student decisions.
The following learning outcomes have been mapped and the corresponding Bloom’s taxonomy level is noted in parentheses. You will see the learning outcomes map to the lower tiers of Bloom’s taxonomy aligning with appropriate learning outcomes for students new to the topics of cybersecurity. There are a few higher tier mappings, allowing for students with prior experience to still benefit from the simulation experience.
The learning outcomes are categorized by cybersecurity simulation role assumed by the student. Student experience and learning outcomes develop over time as the students becomes more engaged with the platform. This is explicitly identified with sub-knowledge objectives based on iterations of simulation experience, and highlights students begin learning as early as the first play through. These learning objectives are intended for a student without prior experience in information security.
Students experience immersion, rules and goals for defending or attacking an IT or OT environment while managing conflicts in a realistic production environment.
Blue Team Learning Objectives
The following learning outcomes align to student experience operating as the “Blue Team”. Bloom’s taxonomy level is included as a preface for clarity and convenience.
- Game level objective (Blue)
- (Evaluate) By the end of the course, students will be able to compare the efficacy and choices in building an information security program.
- (Understand) By the end of the course, students will be able to explain red team and blue team operations and how they relate to each other
- (Understand) By the end of the course, students will be able to generalize techniques to secure an organization’s IT infrastructure
- Course level objectives (Blue first play)
- (Remember) By the end of first play through, students will be able to name different types of cybersecurity controls.
- (Understand) By the end of the first play through, students will be able to discuss the resource costs associated with building an information security program.
- (Remember) By the end of the first play through, students will be able to recognize normal operating conditions and incident response operating conditions
- Course level objectives (Blue multiple plays)
- (Remember) By the end of multiple play throughs, students will be able to label a basic network diagram
- (Understand) By the end of multiple play throughs, students will be able to explain when incident response is activated and why.
- (Remember) By the end of multiple play throughs, students will be able to name different types of vulnerabilities
- (Understand) By the end of multiple play throughs, students will summarize different conditions that could lead to catastrophic organizational failure from a cyber incident
Red Team Learning Objectives
The following learning outcomes align to student experience operating as the “Red Team”.
- Game level objectives (Red)
- (Understand) By the end of the course, students will be able to explain red team and blue team operations and how they relate to each other.
- (Apply) By the end of the course, students will be able to express the order of operations for a successful cyber-attack (i.e., cyber kill chain).
- (Understand) By the end of the course, students will distinguish between Internet-based and on-premises attack techniques.
- Course level objectives (Red first play)
- (Remember) By the end of the first play through, students will be able to name different types of offensive security activities.
- (Understand) By the end of the first play through, students will observe target IT environment visibility increase over time.
- (Remember) By the end of the first play through, students will recall the activity and output of reconnaissance.
- Course level Objectives (Red multiple plays)
- (Understand) By the end of multiple play throughs, students will classify different types of cyber attacks.
- (Understand) By the end of multiple play throughs, students will explain how organizations can be compromised by a cyber-attack over the Internet.
- (Analyze) By the end of multiple play throughs, students will differentiate between denial of service and manipulation attack impacts.
Conclusion
The ThreatGEN® Red vs. Blue Cybersecurity Gamification Platform has educational “scaffolding” incorporated into its design to guide students through the simulation while allowing them to make their own decisions and learning through immersive exploration. This scaffolding manifests in allowing students the choices and paths to pursue that would only be appropriate for that point in the simulation, unlocking decision points when prerequisites are met.
Go to ThreatGEN.com to learn more about how you can take your student engagement, learning outcomes, and curriculum to the next level with the ThreatGEN Red vs. Blue Platform.
Here is a link to the ThreatGEN Learning Objectives in PDF and Microsoft Word formats.
About Gerald Auger, Ph.D.
Dr. Gerald Auger, Ph.D. is ThreatGEN Director of Cybersecurity Education. Dr. Auger holds a PhD in cyber operations, two master’s degrees in computer science and Information Assurance, and has been a cybersecurity professional for more than 17 years. He built and led a cybersecurity program at a $750M manufacturing enterprise and was the cybersecurity architect at MUSC, a multibillion-dollar academic medical center. Because of his passion for cybersecurity and educating others in the discipline, Dr. Auger also teaches at The Citadel Military College, wrote the book Cybersecurity Career Master Plan, and he created the world-renowned and highly successful YouTube channel SimplyCyber.

About ThreatGEN® Red vs. Blue
Founded in 2017, ThreatGEN is “bridging the cybersecurity skills gap” with the ThreatGEN® Red vs. Blue Cybersecurity Gamification Platform. ThreatGEN’s founders and staff have decades of experience in real-world cybersecurity as well as course creation and delivery. The ThreatGEN® Red vs. Blue Cybersecurity Gamification Platform combines this experience with game-based learning and our Active Adversary Simulation™ technology to provide the most advanced cybersecurity training solution on the market.
For more information, visit our company website at https://ThreatGEN.com, follow us on LinkedIn at https://www.linkedin.com/company/threatgenvr/, or follow us on Twitter: @ThreatGEN_RvB.
For further sales information, send an e-mail to sales@threatgen.com.
Derezzed Inc. D/B/A ThreatGEN
+1 (833) 339-6753
#cybsersecurity #gamification
