Since the publication of the SolarWinds attack in December 2020, there have been countless breakdowns of the malware used, how it works, and what the implications are for organizations using Orion products in their IT infrastructure. As extensive as the coverage of the attack has been, we haven’t heard much regarding the risk posed to operational technology (OT) networks and systems by this attack. In this article, we will cover a summary of the attack with some basic, easily digestible, details as well as explore how it can impact OT systems in a hypothetical attack scenario. The SUNBURST malware attack on SolarWinds clients was implemented by injecting malicious code into the Orion platform’s software updates, which compromised their products that received these updates. The attacker could then send commands to the affected software to perform tasks such as file transfer and execution, system profiling, and disabling of system services.
How the SolarWinds malware works
Once the compromised software update is installed, it will wait for several days before beginning its routines. The malware starts by generating a hash from system information such as driver paths and process and service names, which will be checked against a list of known antivirus, monitoring, and other security software. If any of these are detected, services will be disabled one by one until a hash containing no blocked values can be created. The hash will then then be appended as a subdomain to one of the following:
.appsync-api.eu-west-1[.]avsvmcloud[.]com .appsync-api.us-west-2[.]avsvmcloud[.]com .appsync-api.us-east-1[.]avsvmcloud[.]com .appsync-api.us-east-2[.]avsvmcloud[.]com
The malware will then ‘phone home‘ by sending an HTTP request to that subdomain, which will allow our attacker to start sending commands back. Several other domains have also been detected in use with this malware, which include:
avsvmcloud.com digitalcollege.org freescanonline.com deftsecurity.com thedoccloud.com virtualdataserver.com
So far, the list of commands supported by the malware is relatively short, with only 18 commands known. However, it doesn’t take an entire library of commands to cause problems when if malware sits in a position in which Orion platform services are often found. Included are commands to both write to and delete files that can be accessed from the Orion server, which places both the integrity and availability of data in immediate jeopardy on infected networks. Tasks can also be killed or started, which could allow the attacker to take control of processes that have been previously whitelisted or otherwise unmonitored.
Like other network management and monitoring products, Orion relies on Simple Network Management Protocol (SNMP) to collect information and modify behavior of the networked devices. Compromising this puts the attacker in a position to immediately begin profiling your entire network architecture, and any security countermeasures in place. From there, the target asset(s), which can range from file and database servers to IoT devices, as well as any security measures such as firewalls and traffic monitors, can be assessed to determine the next step in the attacker’s goals.
An infected OT network scenario
The implications of an infection of this nature on an IT network can be severe. However, the compromise of an OT network introduces new consequences and impacts that can threaten safety, the environment, and even human life.
OT protocols were by and large created with uptime and availability in mind, in a time where cyber-attacks did not present a prevalent threat. Once access to an OT network is established, an advanced attacker will have multiple tools at their disposal for both the observation and disruption of OT protocols.
Imagine, if you will, a turbine power plant which uses the SolarWinds Orion suite for their IT (but not OT) network management, and the update containing the malicious payload was installed
- Once the malware is ‘activated‘, our attacker begins scanning the network, only to find that the SCADA system controlling plant operation is on a separate network. What they did find, however, is that plaintext FTP is being used to transmit data between the enterprise and production network, which transmits the credentials unencrypted, as well as the data. After collecting the credentials of several users, the attacker uses them to attempt Windows logins, and while not all of the users share passwords between FTP and Windows, one of those that do is an engineer who has full access to the OT network from their workstation.
- So now our attacker has access to the OT network, which they can silently monitor to find connected devices and identify the OT protocols being used.
- We find that the Modbus protocol, a well-known protocol that can be easily manipulated, is being used to transmit critical operational data to PLC‘s ensuring safe operation.
- Suppose that one of these Modbus devices is transmitting steam pressure data back to the PLC, which needs to be kept at an optimal level to ensure both safe and productive operation. While the pressure inside the turbine is stable initially, the PLC begins to receive input of lower pressure.
- To which it responds by increasing the steam flow to the turbine, causing the actual pressure to increase past safe and intended values, ultimately resulting in a catastrophic failure of the turbine.
- If we are lucky, no workers were close to the turbine in question, nobody was hurt, and our only immediate problem is the downtime caused by the supposed mechanical failure. However, if the data manipulation was not detected by any network safety and security solutions, the attacker may be able to strike again in a similar fashion, indefinitely jeopardizing both the safety of plant employees and the ability of the plant to operate reliably going forward.
Our hypothetical network
To paint a better picture of this attack scenario, I’ve included a diagram of our hypothetical target network, with the arrows showing the path taken from the internet to the industrial assets being manipulated, and corresponding numbers to the above scenario to visualize the order of operations here:
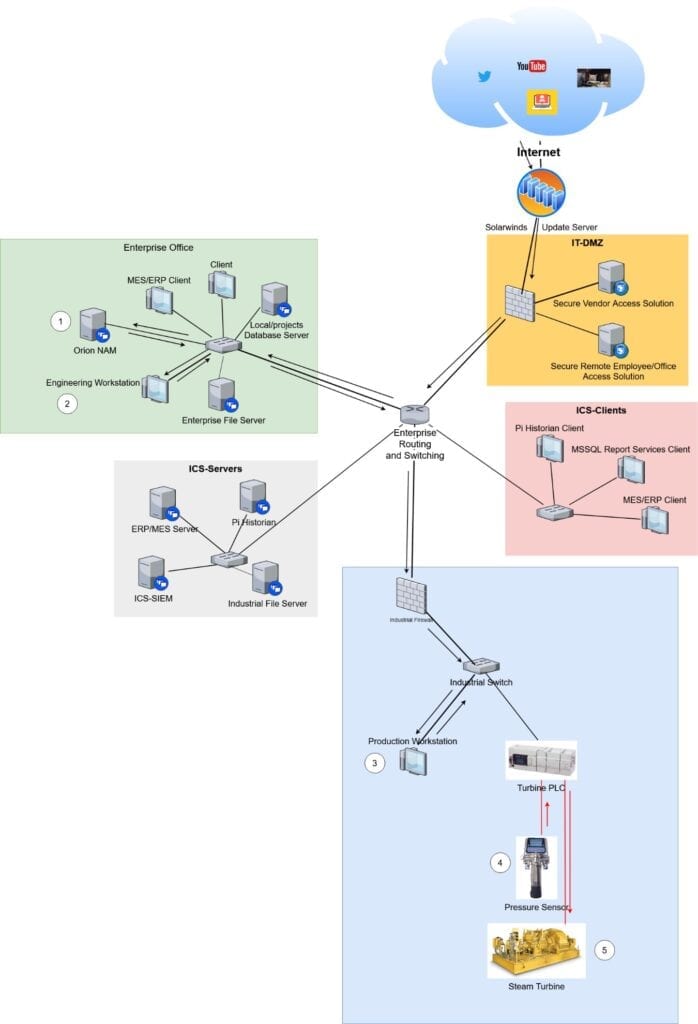
While it can be difficult to anticipate compromises of the software, we use to run our businesses, the risk can be mitigated with the careful implementation of holistic security strategies, such as well-defined access control, network segmentation, and restriction of HTTP traffic to and from external hosts.
Additional indicators of compromises
Additional known indicators of compromise (IOCs) include the following SHA256/SHA1 hashes:
e0b9eda35f01c1540134aba9195e7e6393286dde3e001fce36fb661cc346b91d 16505d0b929d80ad1680f993c02954cfd3772207
a58d02465e26bdd3a839fd90e4b317eece431d28cab203bbdde569e11247d9e2 2546b0e82aecfe987c318c7ad1d00f9fa11cd305
eb6fab5a2964c5817fb239a7a5079cabca0a00464fb3e07155f28b0a57a2c0ed e257236206e99f5a5c62035c9c59c57206728b28
ffdbdd460420972fd2926a7f460c198523480bc6279dd6cca177230db18748e8 fd15760abfc0b2537b89adc65b1ff3f072e7e31c
b8a05cc492f70ffa4adcd446b693d5aa2b71dc4fa2bf5022bf60d7b13884f666 2dafddbfb0981c5aa31f27a298b9c804e553c7bc
20e35055113dac104d2bb02d4e7e33413fae0e5a426e0eea0dfd2c1dce692fd9 d8938528d68aabe1e31df485eb3f75c8a925b5d9
0f5d7e6dfdd62c83eb096ba193b5ae394001bac036745495674156ead6557589 395da6d4f3c890295f7584132ea73d759bd9d094
dab758bf98d9b36fa057a66cd0284737abf89857b73ca89280267ee7caf62f3b 1acf3108bf1e376c8848fbb25dc87424f2c2a39c
32519b85c0b422e4656de6e6c41878e95fd95026267daab4215ee59c107d6c77 76640508b1e7759e548771a5359eaed353bf1eec
cc082d21b9e880ceb6c96db1c48a0375aaf06a5f444cb0144b70e01dc69048e6 e2152737bed988c0939c900037890d1244d9a30e
019085a76ba7126fff22770d71bd901c325fc68ac55aa743327984e89f4b0134 2f1a5a7411d015d01aaee4535835400191645023
ac1b2b89e60707a20e9eb1ca480bc3410ead40643b386d624c5d21b47c02917c 6fdd82b7ca1c1f0ec67c05b36d14c9517065353b
2b3445e42d64c85a5475bdbc88a50ba8c013febb53ea97119a11604b7595e53d c8b7f28230ea8fbf441c64fdd3feeba88607069e
ce77d116a074dab7a22a0fd4f2c1ab475f16eec42e1ded3c0b0aa8211fe858d6 d130bd75645c2433f88ac03e73395fba172ef676
92bd1c3d2a11fc4aba2735d9547bd0261560fb20f36a0e7ca2f2d451f1b62690 2841391dfbffa02341333dd34f5298071730366a
a3efbc07068606ba1c19a7ef21f4de15d15b41ef680832d7bcba485143668f2d
c09040d35630d75dfef0f804f320f8b3d16a481071076918e9b236a321c1ea77 bcb5a4dcbc60d26a5f619518f2cfc1b4bb4e4387
Found in the following files:
C:\Program Files (x86)\N-able Technologies\Windows Software Probe\bin\SolarWinds.Orion.Core.BusinessLayer.dll C:\Program Files (x86)\Solarwinds\Network Topology Mapper\SolarWinds.Orion.Core.BusinessLayer.dll C:\Program Files (x86)\Solarwinds\Network Topology Mapper\Service\SolarWinds.Orion.Core.BusinessLayer.dll C:\Program Files (x86)\SolarWinds\Orion\SolarWinds.Orion.Core.BusinessLayer.dll C:\Program Files (x86)\SolarWinds\Orion\DPI\SolarWinds.Orion.Core.BusinessLayer.dll C:\Program Files (x86)\SolarWinds\Orion\NCM\SolarWinds.Orion.Core.BusinessLayer.dll C:\Program Files (x86)\SolarWinds\Orion\Interfaces.Discovery\SolarWinds.Orion.Core.BusinessLayer.dll C:\Program Files (x86)\SolarWinds\Orion\DPA\SolarWinds.Orion.Core.BusinessLayer.dll C:\Program Files (x86)\SolarWinds\Orion\HardwareHealth\SolarWinds.Orion.Core.BusinessLayer.dll C:\Program Files (x86)\SolarWinds\Orion\Interfaces\SolarWinds.Orion.Core.BusinessLayer.dll C:\Program Files (x86)\SolarWinds\Orion\NetFlowTrafficAnalysis\SolarWinds.Orion.Core.BusinessLayer.dll C:\Program Files (x86)\SolarWinds\Orion\NPM\SolarWinds.Orion.Core.BusinessLayer.dll
For further reading:
- Cybersecurity visibility across the organization, a case study
- Design for Security – Why Proper Architecture Matters to ICS Security
About Jonathan Bundy
Jonathan Bundy is an industrial cybersecurity consultant. He joined ThreatGEN in 2021 after several years as a systems administrator and security analyst for some of the largest names in the web hosting industry. He is passionate about meeting the always evolving challenge of security through honest, thorough evaluation of risk, and sound network design.
About ThreatGEN Threat Services
Founded in Sugar Land, Texas in 0217, ThreatGEN delivers a solution to bridge the Operational Technology (OT) Cybersecurity skills gap” utilizing its ThreatGEN® Red vs. Blue gamification and ThreatGEN Services.
ThreatGEN Services are delivered worldwide by world-renowned OT cybersecurity experts (we literally wrote the books industry uses) using strategically chosen partnerships to create a holistic service offering. The division is led by Pascal Ackerman.

