Posts Tagged ‘cybersecurity’
AutoTableTop™ Version 2.0 Ushers in a New Era for Incident Response Exercises
ThreatGEN anounces AutoTableTop™ version 2.0, a major upgrade to its flagship automated tabletop exercise platform, with availability set before June 1, 2025.
Read MoreUTSI International Joins ThreatGEN Partner Program to Strengthen Pipeline Cybersecurity with AutoTableTop™ Simulations
UTSI International Corporation, a leader in Industrial Control System (ICS) cybersecurity and critical infrastructure protection, has joined the ThreatGEN Partner Program as a Silver Partner. This strategic alliance leverages UTSI’s deep expertise in pipeline operational technology (OT) security and ThreatGEN’s AutoTableTop™ simulation platform to deliver cutting-edge cybersecurity tabletop exercises for critical infrastructure operators.
Read MoreOT-ISAC and ThreatGEN Announce Strategic Partnership
The Operational Technology Information Sharing and Analysis Center (OT-ISAC), managed by GRF Asia-Pacific Pte Ltd, is pleased to announce a partnership with ThreatGEN, a leading provider of cybersecurity simulation solutions.
Read MoreThreatGEN® Welcomes Defend-OT as Gold Partner
Houston, TX (October 14, 2024) – ThreatGEN®, a leader in cybersecurity simulation and gamification-based training, today announced that Defend-OT, a Belgium-based operational technology (OT) cybersecurity firm, has joined its partner program at the Gold level. This partnership aims to enhance cybersecurity preparedness and incident response capabilities for organizations across the Benelux region. As a Gold…
Read MoreThreatGEN® Announces Partnership with Morgan Franklin Consulting
ThreatGEN®, a leader in cybersecurity simulation and gamification-based training, today announced a strategic partnership with Morgan Franklin Consulting (MFC), a prominent cybersecurity consulting and services firm.
Read MoreExciting Updates for AutoTableTop™ Platform
ThreatGEN announces updates and plans for AutoTableTop™ aimed at enhancing user experience and expanding capabilities for its clients.
Read MoreThreatGEN Announces New Features and Major Upgrades to AutoTableTop™ Platform
ThreatGEN announces major upgrades to AutoTableTop™ Platform and Products Features in August 2024 for upgraded customer experience.
Read MoreThreatGEN Announces the Launch of AutoTableTop™: The Future of IR Tabletop Exercises
Houston, TX (January 9, 2024) – ThreatGEN®, an industry leader in cybersecurity simulation and gamification-based training, today announced the release of ThreatGEN AutoTableTop™, a groundbreaking incident response (IR) tabletop exercise platform, redefining cybersecurity incident response preparedness. AutoTableTop™, powered by advanced generative AI, offers a fully automated, customizable, and user-friendly tabletop exercise experience. With unlimited scenarios and…
Read MoreThreatGEN CEO Featured in New Industrial Cyber Article on ICS Incident Response
Industrial Cyber features ThreatGEN Clint Bodungen in an article entitled “Need to Step Up Proactive ICS Incident Response Planning”.
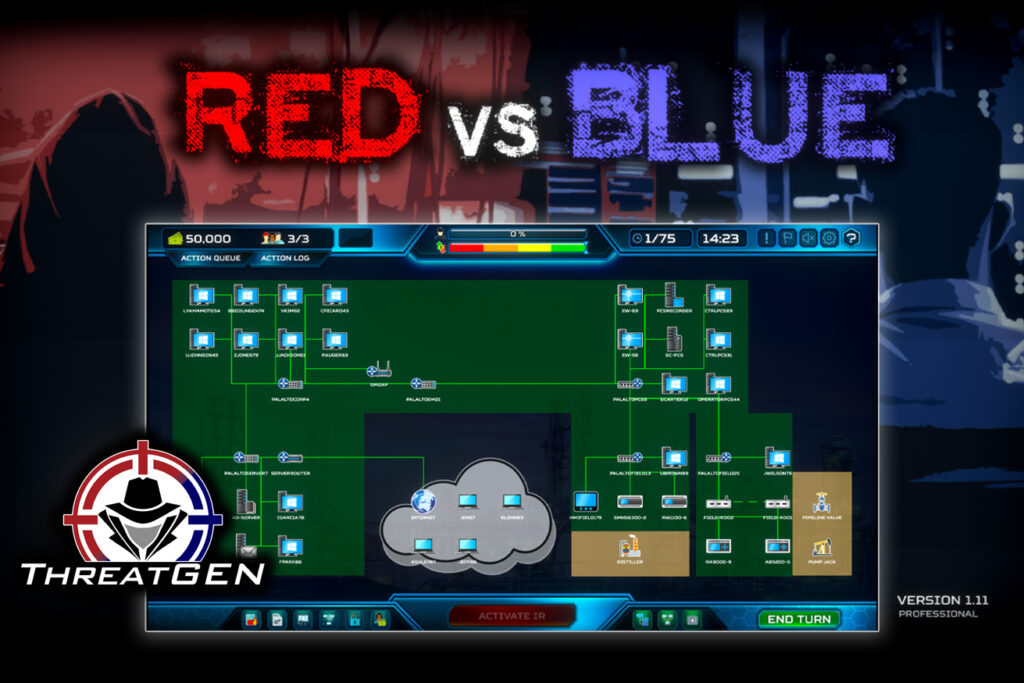
Read MoreThreatGEN® Red vs. Blue Gets Major Upgrade
Red vs Blue v1.11 is here with game-changing updates! This major release adds scenario-based win conditions, new actions for both teams, improved staff management, and more. Cutting-edge AI integration coming soon too. Version 1.11 expands strategic options for the ultimate cybersecurity training experience. Learn more about the exciting new features!
Read More