This latest update, version 1.7, represents a pivotal milestone for ThreatGEN® Red vs. Blue. All of the core features and mechanics are now in place for both the Game Edition on Steam as well as the Professional Edition. Moving forward, our development efforts will focus on enhancing the entire educational experience with eLearning content and curriculums that support our cybersecurity gamification platform, labs and challenges for training curriculums, and several built-in scenarios for incident response (IR) tabletop exercises. But more on all that in a bit. For now, what’s new in this latest update?
New Game Guide
The new game guide helps maximize the simulation and the educational experience. It’s not only a detailed instruction manual on how to play ThreatGEN® Red vs. Blue, but it also includes Red Team and Blue Team strategies and expert advice that apply directly to real-world cybersecurity.
Profit & Loss Meter
Under the version 1.7 threat intelligence score meter, there is a new profit & loss meter. The profit & loss meter represents the financial and production status of the company in relation to cyber outages. When assets are out of service, infected with malware, or having data exfiltrated, the meter will trend downward toward red until the issues are remediated. The more important the asset, the faster the meter will move. When the meter remains in the red for too long, the Blue Team loses.

New Red Team Win Condition
Company Production Compromised added to version 1.7
This win condition is awarded when the Blue Team’s production drops below a threshold for a set number of turns.
New Red Team Actions & Strategies
Malware
Installing disruptive malware is one way to disrupt the productivity (profit and loss) of the Blue Team. The effects can be amplified by using the malware to exfiltrate data.
Ransomware
Ransomware is another devastating tool in the Red Team’s arsenal, which represents one of the most concerning threats in recent times. Unless the Blue Team is lucky enough to have a restore point created prior to the initial compromise, the only recourse they have is to pay the ransom (which is very expensive), crack the ransomware encryption key (which is very difficult to do), or replace the asset. Ransomware is a two-step process. The Red Team must first install ransomware and then activate the ransomware.
New Blue Team Actions & Strategies inversion 1.7
Creating Restore Points
System backups are no longer a “one and done” action that improves your overall chances of cleaning a compromised asset. Now, the system backups action enables the ability to create restore points on each asset as a targeted action. When an asset is infected or compromised, the Blue Team can restore the asset to its last known restore point. However, the last restore point was created after the system was infected or compromised, the asset will still be in the infected or compromised state.
Improved Incident Response (IR)
All IR actions have been organized into their own grouping in the action tree view and several new IR actions have been added to improve the overall IR simulation.
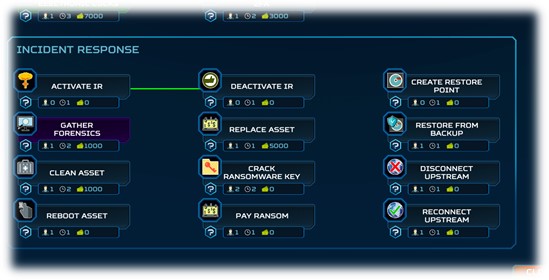
- Restore from backup – As already mentioned the Blue Team can restore from backup if they have created a restore point on the affected asset.
- Disconnect/reconnect the asset from the network – The Blue Team now has the ability to disconnect assets from the network (disconnect from upstream), effectively isolating them and cutting off further malicious activity. As such, the assets can also be reconnected to the network (reconnect to upstream).
- Respond to ransomware infections – Ransomware infections present two additional and unique options. If you have the resources, you can pay the ransomware to recover your infected systems. Or, if you have enough time and security skills training, you can attempt to crack the ransomware encryption key.
What’s Next?
In the first quarter of 2022, we will launch our complete ThreatGEN® Red vs. Blue portal, which is a single point of access to not only the Red vs. Blue cybersecurity gamification platform, but also includes a complete array of cybersecurity education material, eLearning courses, guides, resources, and incident response (IR) tabletop exercise support, all leveraging the ThreatGEN® Red vs. Blue cybersecurity gamification platform. In addition to on demand eLearning courses, the Q1 2022 launch will also feature tons of new ThreatGEN® Red vs. Blue gamification content such as scenarios and labs to support the included courses. Focus on enhancing the analytics and reporting features and dashboards will also be a high priority in early 2022.
For organizations wanting to use ThreatGEN® Red vs. Blue to support their IR tabletop exercises, the portal will include built in scenarios and eLearning content to support guided tabletop exercises ready to go “out of the box” without the need for extensive planning or even a facilitator or instructor.
For those of you wondering about upcoming Downloadable Content (DLC) and expansions for the ThreatGEN® Red vs. Blue Game Edition available on Steam… the answer is YES! Look for DLC for the Steam version by mid 2022 and a single player campaign planned to release later in the year! Finally, with the existing Red vs. Blue tournament features, and new CTF capabilities on the way, 2022 will see the emergence of regularly scheduled ThreatGEN® Red vs. Blue public competitions and events! Be on the lookout for announcements soon!
About ThreatGEN
ThreatGEN bridges the “cybersecurity skills gap” utilizing the ThreatGEN® Red vs. Blue cybersecurity gamification platform powered by our world-renowned OT cybersecurity experts and published authors. The ThreatGEN® Red vs. Blue cybersecurity gamification platform uses cutting-edge computer gamification to provide an exciting & modernized approach to OT cybersecurity training, both practical and cost effective!
For more information, visit our company website, follow us on our LinkedIn page, or follow us on Twitter at @ThreatGEN_RvB. For further sales information, send an e-mail to sales@threatgen.com or fill out our Request for Information (RFI) form.
Derezzed Inc. D/B/A ThreatGEN
+1 (833) 339-6753
#cybsersecuritytraining #cybersecurityawarensss #gamification
